GRANT
- reference
The GRANT statement allows granting any RBAC roles to a specific user.
Roles can be of the following two types:
- simple
-
Roles which apply generically to all keyspaces or resources in the cluster.
For example:
ClusterAdminorBucketAdmin - parameterized by a keyspace
-
Roles which are defined for the scope of the specified keyspace only. The keyspace name is specified after ON.
For example:
DataReader ON `travel-sample`
orQuery_Select ON `travel-sample`
| Only Full Administrators can run the GRANT statement. For more details about user roles, see Authorization. |
Syntax
grant ::= GRANT role [ ',' role ]* [ ON keyspace-ref [ ',' keyspace-ref ]* ] TO user [ ',' user ]*
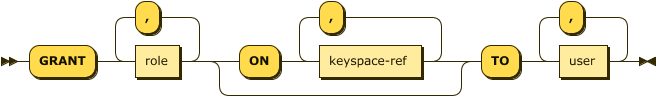
- role
-
One of the RBAC role names predefined by Couchbase Server.
The following roles have short forms that can be used as well:
-
query_select→select -
query_insert→insert -
query_update→update -
query_delete→delete
-
- user
-
A user name created by the Couchbase Server RBAC system.
Keyspace Reference
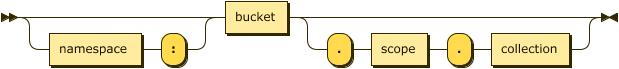
keyspace-ref ::= keyspace-path | keyspace-partial

keyspace-path ::= [ namespace ':' ] bucket [ '.' scope '.' collection ]
keyspace-partial ::= collection
The simple name or fully-qualified name of a keyspace. Refer to the CREATE INDEX statement for details of the syntax.
Usage
GRANT statements support legacy systems and have two forms:
GRANT Replication Admin, Query External Access
TO cchaplan, jgleason;
GRANT replication_admin, query_external_access
TO cchaplan, jgleason;GRANT Query Select, Views Admin
ON orders, customers
TO bill, linda;
GRANT query_select, views_admin
ON orders, customers
TO bill, linda;| Mixing of parameterized and unparameterized roles or syntax is not allowed and will create an error. |