Access Control Concepts
An introduction to the key concepts behind the provision of effective access control in Sync Gateway
The sync function API provides several methods that you can use to validate and control user access to databases and documents.
Related Concepts: Access Control Model | Channels | Roles | Sync Function | Users
Access Control Model
Concept
You control document access by routing it to a channel and by making that channel accessible to the users or roles you want to be able to access documents of that type.
Model
In the Couchbase Mobile ecosystem access to documents is governed by three key entities: users, roles and channels.
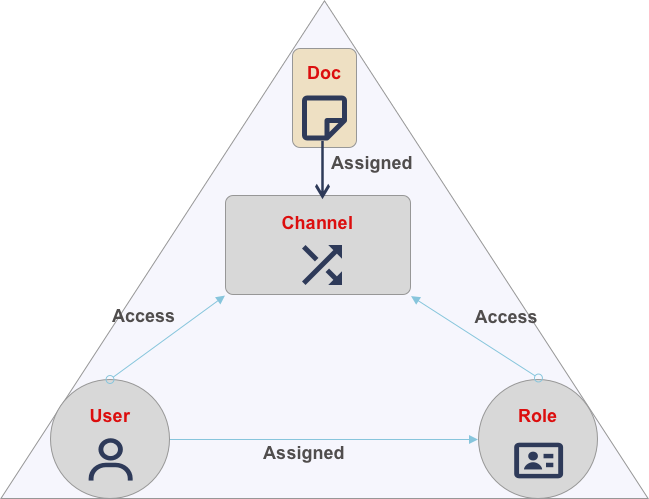
Conceptually, the channel can be considered as a tag associated with a document. Every document processed by the Sync Gateway is assigned to a channel (user-defined or system-defined). A channel is the fundamental way to segregate documents and for enforcing access control.
Every Sync Gateway user is granted access to zero, one or more channels. It is the channels membership that determines the documents users can access — as illustrated in Access Control Model
A Sync Gateway role is a way of logically grouping users. Like the channel, a role is granted access to zero, one or more channels.
A user can only read documents that are in at least one of their assigned channels; whether directly or as part of an assigned role.
Context
You control document access by routing it to a channel and by making that channel accessible to the users or roles you want to be able to access documents of that type.
Sync Gateway
All users can implicitly access any document in the public channel. In addition, there can be user-defined channels that users can be assigned to.
Once a user is granted access to a new channel, the next replication pull request from the client will retrieve all documents to which the user now has access.
Revoking access to a channel means that users who previously used the channel to get replicated documents will no longer see any synced updates.
Note that access grants neither confer, nor constrain, the type of access. Instead you can explicitly implement write access controls within the Sync Function; perhaps restricting updates to specific users or roles — for more on this see Control Write Access.
Couchbase Lite
By default, Couchbase Lite gets all the channels to which the configured user account has access. Optionally, a Couchbase Lite "pull" replication can also specify a comma-separated list of channel names to receive documents from. In this case, the replication from Sync Gateway will only pull documents tagged with those channels. Client apps can use this ability to intelligently sync with a subset of the available documents from the database.
Channel Access Revocation
|
3.0 Breaking Change
Whenever a user loses access to a channel (or channels) all document in the channel(s) are auto-purged from local Couchbase Lite databases.In Sync Gateway 2.x these documents remain in the local database on channel access loss. |
Users may lose access to documents for many reasons, including:
-
The User loses direct access to channel
-
The User is removed from a role
-
A role the user belongs to is revoked access to channel
By default, when a user loses access to a channel, the next Couchbase Lite Pull replication auto-purges all documents in the channel from local Couchbase Lite databases (on devices belonging to the user) unless they belong to any of the user’s other channels — see: Table 1.
| System State | Impact on Sync | |
|---|---|---|
Replication Type |
Access Control on Sync Gateway |
Expected behavior (auto-purge enabled- default) |
Pull only |
User revoked access to channel. Sync Function includes |
Previously synced documents are auto purged on local |
Push only |
User revoked access to channel. Sync Function includes |
No impact of auto-purge Documents get pushed but will be rejected by Sync Gateway |
Push-pull |
User revoked access to channel Sync Function includes |
Previously synced documents are auto purged on Couchbase Lite. Local changes continue to be pushed to remote but are rejected by Sync Gateway |
Provisioning
-
Channel — the channels topic discusses how channels are created and how documents can be assigned to channels.
-
User — the user topic discusses provisioning of users and providing users access to channels.
-
Role — the role topic discusses roles, assignment of users to roles created and providing roles access to channels.
Channels
Concept
Sync Gateway uses Channels to make it easy to share a database’s documents across a large user base whilst retaining effective access control. They serve as a security conduit between the document and a user:
Overview
Every document in the database is assigned a list of channels it is distributed to. Every user (or role) is granted access to a list of channels. This dual-purpose is reflected in the way you use channels:
-
By granting a user access to a channel, you are imposing access control
-
By assigning a document to a channel you are imposing document routing
You typically will use channels to:
-
Control who can access what
-
Partition your data set
-
Enable users to access just the documents they need
-
Minimize the amount of data synced to mobile devices
Sync Gateway provides two special channels and a channel wildcard character.
Use Case
Consider the case where two users require, and are allowed, access to a private set of documents and one shared set of documents — see Figure 1.
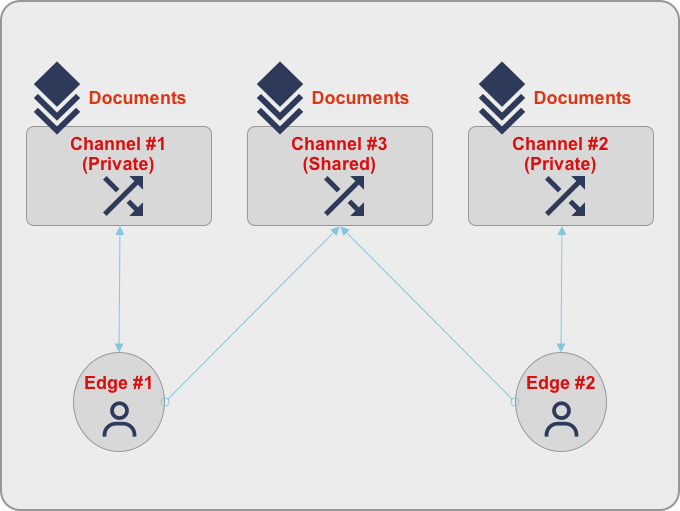
In this case, each user is assigned to a private channel with a subset of documents that only the user can access and a shared channel that contains common documents. The users in this example could be replaced by roles.
An example of this model could be a retail chain, where every store corresponds to a Sync Gateway User. Each store has a store specific channel that contains documents that are store specific like pricing, promotions, inventory etc. In addition, all the stores may need to have access to a common set of documents like retail locations, product catalog that are stored in a common shared channel.
Configuration
-
Version 3.x
-
legacy
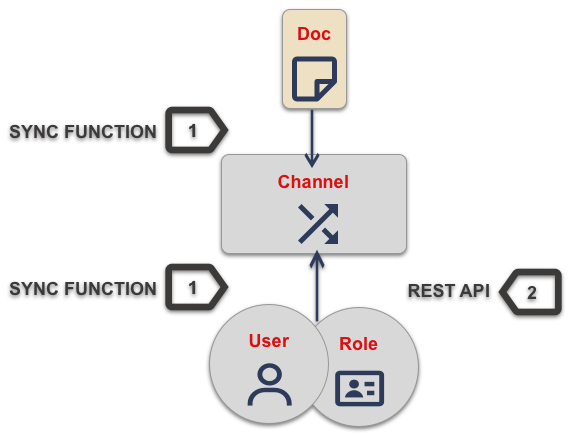
| 1 | Using the Admin REST API: You can provide the admin_channels property using the Admin REST API endpoint (/{db}/_user/{name}). |
| 2 | Programmatically using Access Grant Document: The Sync Function provides a flexible and secure method for controlling document access and routing. You can program it to derive appropriate access and channel routing information from document properties. Optionally, the access grant can be specified via a designated extended attribute (XATTR) — see: Use XATTRs for Access Grants for how to define the XATTR. |
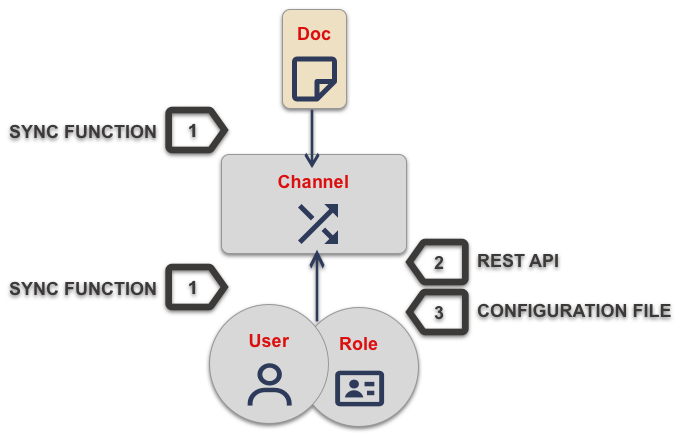
| 1 | Using the Admin REST API :
You can provide the admin_channels property using the Admin REST API endpoint (/{db}/_user/{name}). |
| 2 | Programmatically using Access Grant Document:
The Sync Function provides a flexible and secure method for controlling document access and routing. You can program it to derive appropriate access and channel routing information from data embedded within document properties. |
| 3 | File-based Configuration Properties: This is only available in 3.x and is typically used for dev/test environments. You can do it in the Sync Gateway JSON Configuration File (Database Configuration ) by adding the appropriate channel to the user’s admin_channels property — see: user admin_channels. |
System Channels
Public Channel
The Public Channel ('!') — is a channel for publicly available documents. It is ideal for use in making information available across the user community.
You assign a document to the public (!) channel using the channel() function.
Documents assigned to this channel can be accessed by all users; even users assigned no specific channel access.
New users are automatically granted access to the channel.
All Documents Channel
The All Documents Channel ('*') [1] — is a single, internal channel, comprising all documents from all channels.
Assignment to this channel is automatic and implicit. You cannot explicitly assign documents to the channel or remove documents from it.
This channel should not be confused with the use of the All Channels Wildcard in access grants.
All Channels Wildcard
The All Channels Wildcard ('*') — used when granting user access, this wildcard grants access to any document in any channel.
You make dynamic user access grants in the sync function using the access() method.
Granting a user access with the all channels wildcard gives them access to any channel, and any document in any channel, including those from private channels.
Replications by users with all channels wildcard access will pull all documents. Because of this potential for syncing large volumes of data (sync pulls all documents in the bucket), users with all channels wildcard access should use a channel filter to explicitly name the channel(s) to be sync’d.
Note: Users granted access using the all channels wildcard do not inherit requireAccess() rights to any specific channel.
| Always use a filter in conjunction with the all channels wildcard, to avoid sync unnecessarily pulling large numbers of documents to mobile devices. |
You assign documents to channels in the Sync Function.
Channels are created as documents are assigned to them.
Valid channel names consist of text letters [A–Z, a–z], digits [0–9], and a few special characters [= + / . , _ @].
Channel names are case-sensitive.
Channels with no documents assigned to them are empty.
Channel Limits
| Element | Limiting factor | Guidance Limit (Channels) |
|---|---|---|
Channels per document |
The amount of memory consumed by the combined number of channels and access grants must fit within the maximum 1Mb xattr size limit — see: Table 3. |
50 |
Channels per user |
The amount of memory consumed by channels must fit within the 20 MB available on Couchbase Server docs for storing metadata — see: Table 3 |
1,000 |
Sync Metadata Limits
Every time a document is assigned to a new channel, the channel name is appended to that document’s sync metadata.
Therefore, a document’s set of channels is limited by the allowed sync metadata size described in Table 3.
Value of enable_shared_bucket_access |
Size (Mb per Document) |
|---|---|
|
20 |
|
1 |
Sync Gateway will assign a document to a new channel as long as the sync metadata remains under the allowed limit.
What to do when your channel count exceeds the usable space for sync metadata?
In order to lower the sync metadata size per document, you can do one of the following:
-
Lower the number of channels per document.
-
Shorten the channel names. A shorter channel name will occupy less space ("customer==0030169303" vs "cs==0030169303").
-
Lower the revs_limit value. Indeed, a copy of channel metadata is retained for each revision of a document.
Users
Concept
Users are one of the cornerstone concepts of access control. You can restrict document access to specific users and-or to users with specific roles.
Sync Gateway Users
Sync Gateway users and roles have no relationship to Couchbase Server’s RBAC (Role-based Access Control) users. They are created and operate solely within the Sync Gateway ecosphere to govern access to replication data and to the Public API.
Users granted access to a Channel can access all documents assigned to that channel.
Users can also be assigned to zero or more Roles. A user inherits the channel access of all roles it belongs to. This is very much like Unix groups, except that roles do not form a hierarchy.
Sync Gateway user credentials can be used to authenticate access to the Public API; RBAC users are required for access to other API.
RBAC Users
Couchbase Server RBAC user credentials are required to authenticate and authorize access to the Admin and Metrics API. You will need to create these users on Couchbase server in order to enable access — see: Create RBAC users for how to and Security Authorization Overview for more on RBAC user authentication.
Roles
Concept
Roles are named collections of Channels. They enable the grouping together of Users with similar characteristics, which makes the management of large user populations easier.
Roles are granted access to channels. Any user assigned a role can access any channels (and documents within those channels) the role has been granted access to.
As an entity, roles comprise a name and a list of channels.
Any user associated with a role inherits the right to access any of the channels in the role’s list. This provides a convenient way to associate multiple channels with multiple users.
| Roles have a separate namespace from users, so it’s possible to have a user and a role with the same name. |