GRANT
- Capella Operational
- reference
The GRANT statement allows granting any RBAC roles to a specific user or group.
Roles can be of the following two types:
- simple
-
Roles which apply generically to all keyspaces or resources in the cluster.
For example:
cluster_adminorbucket_admin - parameterized by a keyspace
-
Roles which are defined for the context of the specified keyspace only. Specify the keyspace name after the keyword ON.
For example:
data_reader ON `travel-sample`
orquery_select ON `travel-sample`.`inventory`.`airline`
To run the GRANT statement, you must be an Organization Owner or Project Owner.
|
Syntax
grant ::= grant-user | grant-group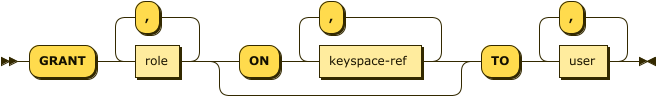
grant-user ::= 'GRANT' role ( ',' role )* ( 'ON' keyspace-ref ( ',' keyspace-ref )* )?
'TO' ( 'USER' | 'USERS' )? user ( ',' user )*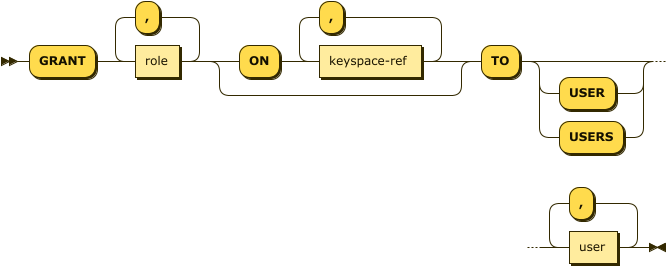
grant-group ::= 'GRANT' role ( ',' role )* ( 'ON' keyspace-ref ( ',' keyspace-ref )* )?
'TO' ( 'GROUP' | 'GROUPS' ) group ( ',' group )* 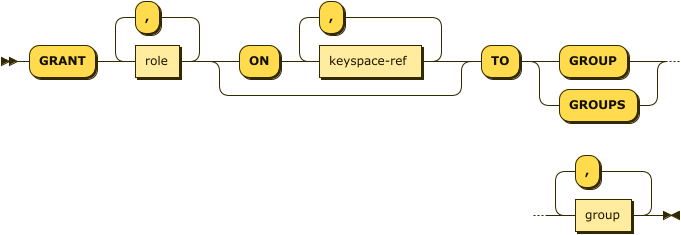
| role |
One of the RBAC role names predefined by Couchbase Capella. For the following roles, you can use their short forms as well:
|
| keyspace-ref | |
| user |
A user name created by the Couchbase Capella RBAC system. |
| group |
A group name created by the Couchbase Server RBAC system. |
When granting roles to users, the keyword USER or USERS is optional.
However, when granting roles to groups, you must include the keyword GROUP or GROUPS.
You can use either the singular or plural form of these keywords as this does not affect the number of users or groups the role applies to.
|
Keyspace Reference
keyspace-ref ::= keyspace-path | keyspace-partial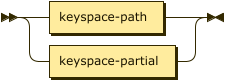
keyspace-path ::= ( namespace ':' )? bucket ( '.' scope '.' collection )?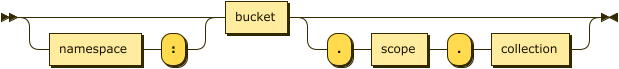
keyspace-partial ::= collection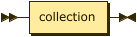
The simple name or fully qualified name of a keyspace. For more information about the syntax, see the CREATE INDEX statement.
Usage
GRANT statements have two forms:
GRANT replication_admin, query_external_access
TO cchaplan, jgleason;GRANT query_select, views_admin
ON orders, customers
TO bill, linda;| Mixing of parameterized and unparameterized roles or syntax is not allowed and will create an error. |
Examples
GRANT cluster_admin TO david, michael, robin;travel-sample keyspace to a specific userGRANT query_select, data_reader ON `travel-sample` TO debby;travel-sample keyspace to a specific groupGRANT data_reader ON `travel-sample` TO GROUP sales;